updated: 2024-04-17
Description
I came across this and find it very useful in a breakdown of all the different ways to reference security standards and where/how they are applied. I find this a lot easier to comprehend and digest than going through the CISSP in some circumstances. I’ll be uploading pieces of it as I find the best way to display the inforomation.
Sections Include:
- Overview
- Risk Managment
- Network Security
- Access Management
- Application Security
- Data Security
- Operational Security
- BCDR
- Department of Defense Risk Mangement Framework
- Cloud Frameworks
- Container Security
- Application Container Security Guide
See Also: RestAPI
NOTE: Working on a cloud section.
Overview
download
Page: /
back to top
Risk Managment
Given a set of requirements apply the appropriate risk strategies. Risk Management is trying to protect your organizations data which is apart of the Governance, Risk, and Compliance measures taken to guard against unlawful use or advisories.
Risk Mangement includes:
There are 3 types of Risks:
- Inherent Risks
- Residual Risks
- Risk Exceptions
Calculations of risk is necessary in order truely understand and set up the proper safeguards against the assessed risk.
back to top
Network Security
Security Architecture is to analyze the security requirements and objectives to ensrue an appropriate, secure network architecture for a new or existing network. It is always important to remember to build and design with security in mind to make expansions easier if designed with security at the begining.
All vendors promise to deliver on all security measures, but one should always be cautious as that is almost never going to be the case.
Security Design Considerations:
- Network Architecture
- Unique use case to your organization
- Newtowrk design’s future and alignment with your busines
back to top
Access Management
Athentication and Authorization is primary concern around controls for Access Management.
Concepts Surrounding Access Control:
- Access Control
- Mandetory Access Control
- Descressionary Access Control
- Rule Based Access Control
- Attribute Access Control
- Credential Management
- Password Repo
- Hardware Key Management
- Multifactor Authentication
- One Time Passwords
- HMAC
- Time Based
- Federated Authorization
back to top
Application Security
Software Applications are a focuse on Security Architecture where you must integrate software applications securely into an enterprise architecture.
Application Level Security includes:
- System Development Life Cycle
- Software Development Life Cycle
- Development Approaches
- Software Asurance
- Secure Design Patterns and Standards
Three Types of ways to secure:
- Secure by design
- Applications are properly designed and coded from the begining.
- Secure by default
- Applications considered secure without any changes to its settings.
- Secure by deployment
- Accouts for applications environment, which relies on the environment around the application handling the security on behalf of the application.
back to top
Data Security
Seucrity practitioners should unite teams to achieve data security. As data security controls tend to touch on many different dapartments throughout an organization when it comes to data and the sensitivity of said data.
Data Security includes:
- Data life cycle
- Data storage
- Obfuscation
- Data Loss Prevention/Detection
back to top
Operational Security
Operational Securtiy (OPSEC), also known as prcedural security, is a risk management process that encourages managers to view operations from the perspective of an adversary in order to protect sensitive information from falling into the wrong hands.
resource
back to top
BCDR
A Business Continnuity and Disaster Recovery is a system of prevention and recovery from potential threats to a company. The plan ensures that personnel and assets are protected and are able to function quickly in the event of a disaster.
KEY TAKEAWAYS:
- Business continuity plans (BCPs) are prevention and recovery systems for potential threats, such as natural disasters or cyber-attacks.
- BCP is designed to protect personnel and assets and make sure they can function quickly when disaster strikes.
- BCPs should be tested to ensure there are no weaknesses, which can be identified and corrected.
What is BCDR?
back to top
Department of Defense Risk Mangement Framework
The US Department of Defence (DoD) has adopted the DoD Risk Management Framework (RMF). Based on a six-stage model and publishedvia the guidence of the National Institute of Science and Technology (NIST).
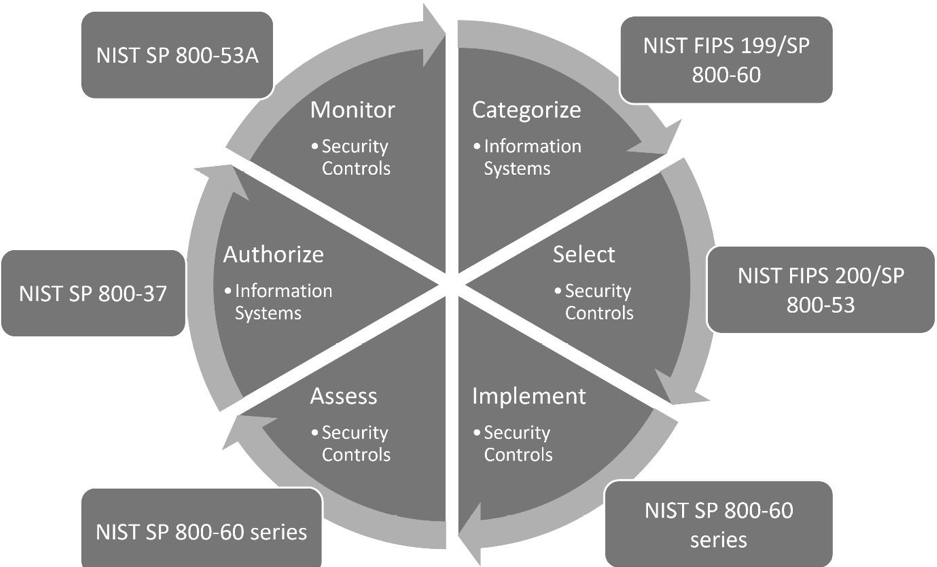
DoD Instruction 8510.01
back to top
Cloud Frameworks
NIST Cloud Computing Standards Roadmap publication 500-291 v2
NIST Cloud Computing Standards Roadmap
back to top
Container Security
Application Container Security Guide
Abstract: Application container technologies, also known as containers, are a form of operating system virtualization combined with application software packaging. Containers provide a portable, reusable, and automatable way to package and run applications. This publication explains the potential security concerns associated with the use of containers and provides recommendations for addressing these concerns.
NIST SP 800-190
back to top