Cloud Considerations
updated: 2023-02-24
Table of Contents:
- Overview
- Considerations
- Where do I start?
- Cloud Native vs Cloud Agnostic
- Nework Segmentation & Hiearchy
- Network Segmentation
- Network Hierarchy
- Security
- Firewall
- Cloud Workload Protection
- Protect Your Cloud
- References
Overview
Going to the cloud can be a difficult journey and has a lot of obsticles around it. Let’s try to break down those obsticles leveraging publications and information readily availble to help you get through your cloud journey.
Considerations
Going into the cloud should be a well thought out process planned as far in advanced as possible. Too many times I see organizations just jump into the cloud becuase:
- It’s easy to get something up and running.
- Business requirements want/need something up and running ASAP.
- False sense of security around cloud.
- Missunderstaning of how to leverge existing guidlines in proper cloud deployments.
Where do I start?
First you need to know what kind of deployments you are looking to do and what cloud is best for those tasks. Not all cloud providors are created equal and each one has it’s pros and cons. Selecting one cloud over the others will always come down to the individual customer’s wants and needs. I think User Guiding Computing Services
has done a good breakdown on the pros and cons of the major Cloud providors.
In summary:
- AWS Cloud
- Major challenge with AWS is always around pricing/cost.
- In my experience they tend to change things around a lot; which I guess could be a good thing that shows they are trying to inovate.
- Has an abondance of offerings for multiple use cases giving you all types of options, but heavily seen in specific markets.
- Google Cloud Platform (GCP)
- Well lets say Google Cloud is the birthplace of Kubernetes, which was originally developed at Google and released as open source in 2014 ref
.
- Google Cloud Platform has been considered user friendly and straight forward.
- Is a security-oriented cloud computing services.
- Is a one stop shop for AI machine learning engineering models. Check out Vertex AI
- Microsoft Azure
- Many flock to Microsoft Azure due to already having a strong foothold into organiztions, which offer an ease of integrations. Think:
- Windows Server
- Sysem Center
- Active Directory
- Microsoft Dynamics 365 Business Central
Cloud Native vs Cloud Agnostic
So, lets say you are in a situation where you want full redundancy. Becuase lets face it just because you are in the cloud and build out all the High Availbility you possibly can; this won’t stop a major outage that has happened to any/all of the providors listed at one point or another. Maybe you want to go for a hybrid solution.
Cloud Native is an architectural style where the application is typiclly one that is designed to run on a specific platform. Once you go cloud native porting over to a new cloud company can become such an impedence that you are now stuck with that company. And as cloud is ever evolving and the competion out there is tough any one of the major providers can become leaders or specialize in something you as a company want to fully take advantage of. But if you are building just for a single cloud solution than you are stuck costing millions to re-write and re-architect your systems to fit into another cloud solution.
Cloud Agnostic is an architectural strategy that focuses on designing applications that can run seamlessly in any cloud environment. Cloud-agnostic applications and services are not dependent on the limited toolchains of one major cloud platform. Allowing you the flexiblity to move between cloud competitors or even possibly leverage two competting cloud company’s to further keep your applications up and running.
side story, and I don’t know how they accomplished this, but there was this company that needed a two management systems up and running to manage and handle all their cloud security products. They set it up to have a primary set up in AWS with a secondary in Azure and are able to sync the two systems to ensure if one cloud vendor had a major outage the other vendor would hopefully not be affected by that same issue.
Nework Segmentation & Hiearchy
Granted a lot of these concepts come from traditional networking, but what is cloud but a culmination of years of developming different tools and systems now all coming together into a virutalized environment.
These are all building blocks that make up our on-prem security, so why would we take any different approach when looking at the cloud?
Building out proper segementation and hiearchy is essential to increase your public cloud security. And this is not just me saying this read TechTarget Network Segmentation article
. It direclty points out the advantages of network segmenation in the cloud. Also check out: Gartner Network Segmentation Blog
Network Segmentation
Network Segmentation is the pratice of dividing up a computer network into multiple subnets in order to improve performance, stability, and leads to better security practices.
Network Hierarchy
A hierarchical IP address design means that addresses are assigned in a hierarchical manner, rather than randomly. The telephone network provides a good analogy (I know it’s old, but it was a well thought out system and look how long it has lasted). This network is divided into countries, which in turn are divided into areas and local exchanges. Phone numbers are assigned based on location.
An IP network can use a similar hierarchical structure to get comparable benefits. When routers only have summary routes instead of unnecessary details, their routing tables are smaller. Not only does this save memory in the routers, but it also means that routing updates are smaller and therefore use less bandwidth on the network. Hierarchical addressing can also result in a more efficient allocation of addresses as well as lead to better security controls since your IP schematics become more predictable.
And what is networking, but the foundation of security. Before firewalls we used subnets to control what segments could talk to what. We should consider this when going into the cloud and ensure a proper layout and design. Now also add in a hiearchy that is easy for your engineers to follow. I learned this very early on in my career. I worked for an organization that had such a good network layout that you could tell what part of the world, what region of the world, and what datacenter data was flowing from simply by looking at the IP Address’s octets and determining what subnet it belonged to. This was astonishing to me. I’ve tried to replicate this anywhere I go.
Security
Now that we got Network fundimentals out the way it’s time to start building out the security on top of it. You already have a good foundation with segmentation and being able to now identify what Cloud you are in what region you are in and what type of environment you are in. If you got the basics of your Network Segementation and Network Hiearchy down right.
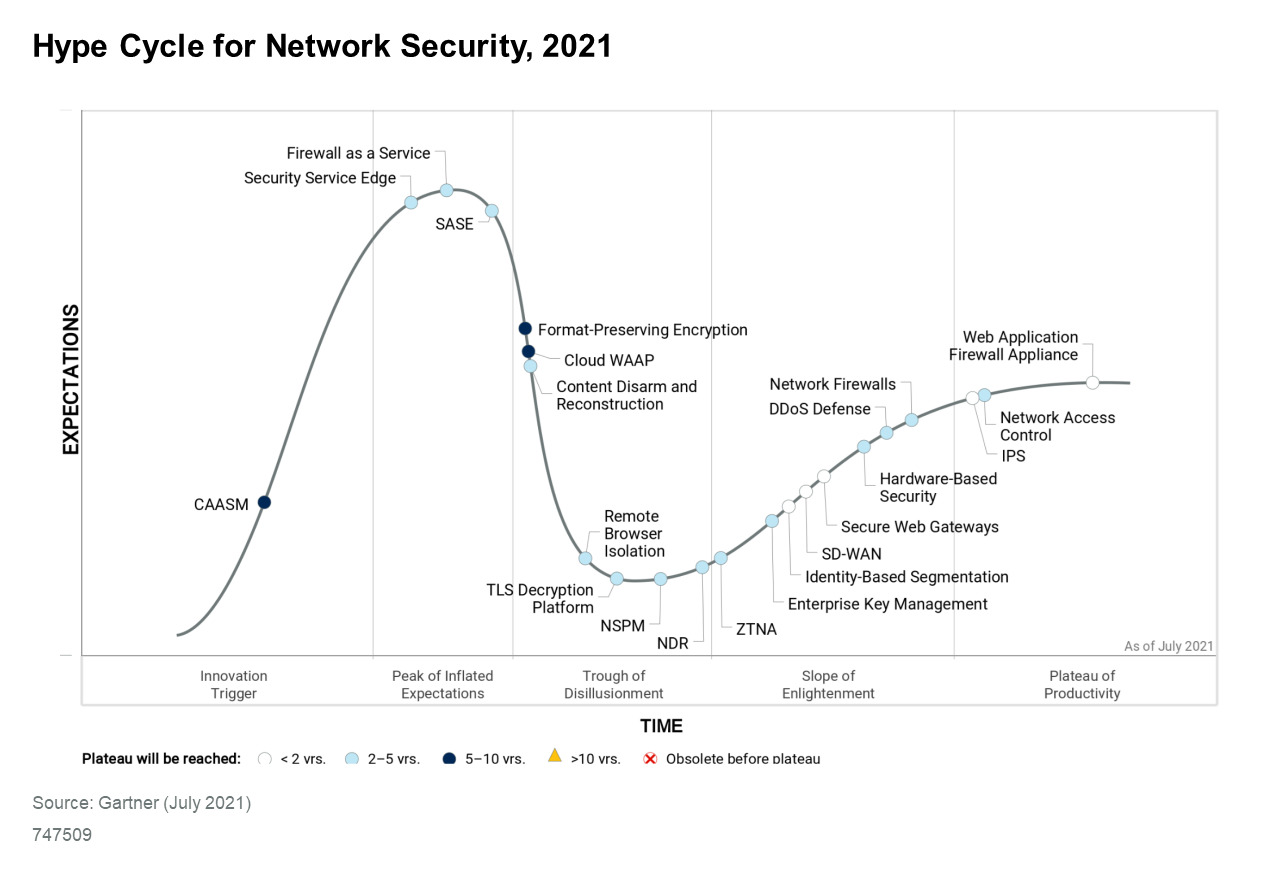
Some of the most beneficial changes this year have been in the area of SASE. By pursuing a consolidation strategy in network security, it increases ease of use of network security tools, and reduces complexity with modular tools and licensing. SASE security services is an extension into a single-vendor, cloud-centric converged capability. - Gartner Hype Cycle for Network Security, 2021
Firewall
I have some evaluations of Palo Alto based products that you can go to review some in depth analysis and deployment practices. Primarily centered around AWS, but they can be built to be cloud-agnostic solution to help with any cloud of choice. Besides the limitations seen in AWS Firewall Manager
and how the defensive strategy comes, in my opinion, from a coder first approach rather than a security first approach. These solutions offer a more defensive-in-depth
solution that can be ported and re-used:
In those articles I review how we manage and secure AWS traffic between VPC’s and how we can automate policy creation via tags. I have the luxary from Palo Alto to be able to test and help out with their brand new Cloud NGFW
product. And I am hoping with a lot more work that will be the future.
Cloud Workload Protection
Cloud Workload Portection Platforms (CWPP) is not a new concept, but have evolved over time.
As CWPP strategies can no longer rely solely on preventive controls, server workload behavioral monitoring is becoming a critical requirement. The increasingly short life spans of workloads means there is no time for traditional loading of signature files or anti-malware scanning. But there is so much more to modern CWPP solutions than meets the eye. Gartner offers a hierarchical view of the intricate CWPP mechanism that should serve as a foundational resource for all prospecting customers. ref
You’ll also see company’s like Palo Alto
and Aqua
that are taking CWPP and Comprehensive Security Poster Management (CSPM) and creating a new category of protection called Cloud Native Applicatio Protetion (CNAPP).
Here is a Gartner pyramid diagram of the controls hiearchy:
{{ < figure src="/images/gartner_cwpp_controls_hierarchy.jpg" width=“20%” height=“20%” > }}
I would just like to point out a common theme here is always the foundation which is Networking, Firewall, and Microsegemenation (or segmentation, but microsegmentation is where traditional datacenters have been slowly moving to although this is anohter topic in-itself).
Protect Your Cloud
We have only delved into Cloud Workload protections above, but in order to achieve a full defense-in-depth solution, we now need to go up the stack and as we grow more and more serverless we need to ensure we are protecting intra stack communications that may not pass through a traditional firewall. Palo Alto always comes to mind as that is my background and I work heavily with them.
Palo Alto Networks Prisma Cloud has taken top honors in three categories of the 2022 SC Awards
, including:
- Prisma Cloud
named the Best Cloud Workload Protection Solution
- Idan Tendler, vice president of Code Security for Prisma Cloud (Bridgecrew), honored as Innovator of the Year.
- “
We've Got Next
” named Security Marketing Campaign of the Year
There are alternatives. What I end up seeing though is company’s with nothing but an alphabet soup of different tools trying to merge them all together to make security work. That generally happens when a company doesn’t sit down and iron out what they want from end to end. It also tends to happen in companies still in a traditional silo’ed environmemnt where one hand doesn’t understand what the other is doing.
If you are not a Palo Alto fan or even want to go down that pathway you have tools such as:
- Amazon CloudFront
- Akamai
- CloudFlare
- Fastly Next-Gen WAF
- AquaSec
- Qualys
- Rapid 7
There are so many tools out there, but ultimately it is up to you and your organization how you want to follow through with your cloud security.
References